Firewall rules
Cloudera requires that you pre-create a set of firewall rules allowing your organization SSH and UI access to Cloudera and allowing internal communication between Cloudera components. Cloudera does not offer an option to create these firewall rules for you.
You have two options:
| Option | VPC type supported for this option | What to do during environment registration |
|---|---|---|
|
Per project VPC Shared VPC |
In this case, you do not provide them to Cloudera during environment registration (That is, during environment registration you select "Do not create firewall rule"). |
|
Per project VPC | In this case, you should select the firewall rules created for SSH and UI access during environment registration |
Firewall rule requirements
You can add firewall rules in Google Cloud directly at the VPC level or via the security access control mechanism from VPC network > Firewall > Create firewall rule. For instructions on how to create and manage firewall rules in GCP, refer to Using firewall rules in Google documentation.
The firewall rules that you add should:
- Allow the instances in the VPC to connect with each other using TCP and UDP
protocols on any port. To achieve this, add a TCP/UDP rule that is set to the subnet IP
range. This is required for internal communication within the VPC. As an example, see
the intravpcconnection firewall rule, which is set to the subnet IP range
(
10.0.0.0/16) in the following screenshot: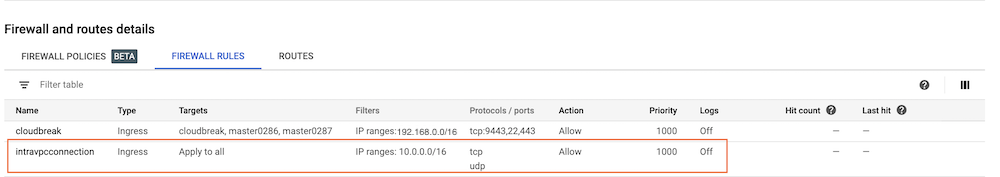
- Open TCP ports 22 and 443 to allow access from your organization's CIDR.
- If not using Cluster Connectivity Manager, also open TCP port 9443 to allow access from Cloudera CIDR.
- If not using Cluster Connectivity Manager, also open TCP port 443 to allow access from Cloudera CIDR. This is required for the gateway nodes.
- Open TCP/UDP ports 0-65535 to your VPC’s CIDR (for example 10.10.0.0/16) and your subnet’s CIDR (for example 10.0.2.0/24).
- Allow ICMP traffic from your internal VPC CIDR (for example 10.10.0.0/16).
